
【AWS re:Invent 2024】Uncovering sophisticated cloud threats with Amazon GuardDuty セッションレポート
re:Invent2024
株式会社サイバーセキュリティクラウド
投稿日:2025/03/13
AWS re:Invent 2024で開催された、「Uncovering sophisticated cloud threats with Amazon GuardDuty」 のセッションのレポートをお届けします。
セッションの概要
本セッションは2024/12/1に発表されたGuardDutyの新機能についてのBreakout Sessionでした。
https://aws.amazon.com/about-aws/whats-new/2024/12/amazon-guardduty-extended-threat-detection/

セッションの冒頭で、スピーカーのシニアセキュリティスペシャリストの方が、本日紹介する新機能はここ数年のGuardDutyの中で最も大きなローンチと述べており、機能の有用性とその興奮が伝わってきました。
前半はGuardDuty自体の概要やカバレッジが説明されていましたが、本レポートでは割愛いたします。
GuardDuty Extended Threat Detectionの紹介

サイバー攻撃は一般的に多段階攻撃で行われます(情報収集、侵入、機密データ搾取、証跡ログの隠滅等)。
これまでGuardDutyは1つ1つのアクティビティを個別に脅威判定してFindingsを出力していたので、そのFindingsが多段階攻撃の一連の攻撃シーケンスかどうかは、セキュリティの専門家が人手で判断する必要がありました。
今回のアップデートにより、GuardDutyが24時間の時間枠で行われた複数のリソースとデータソースにまたがるアクティビティを相関分析して(複数のセキュリティシグナルの組み合わせ)、攻撃シーケンスかどうかを判定してくれるようになりました。
本機能を活用することで個々のFindingsの分析に費やす時間を削減して、最も優先度が高い脅威に集中することができます。
本機能はデフォルトで有効になっており追加費用はかかりません。
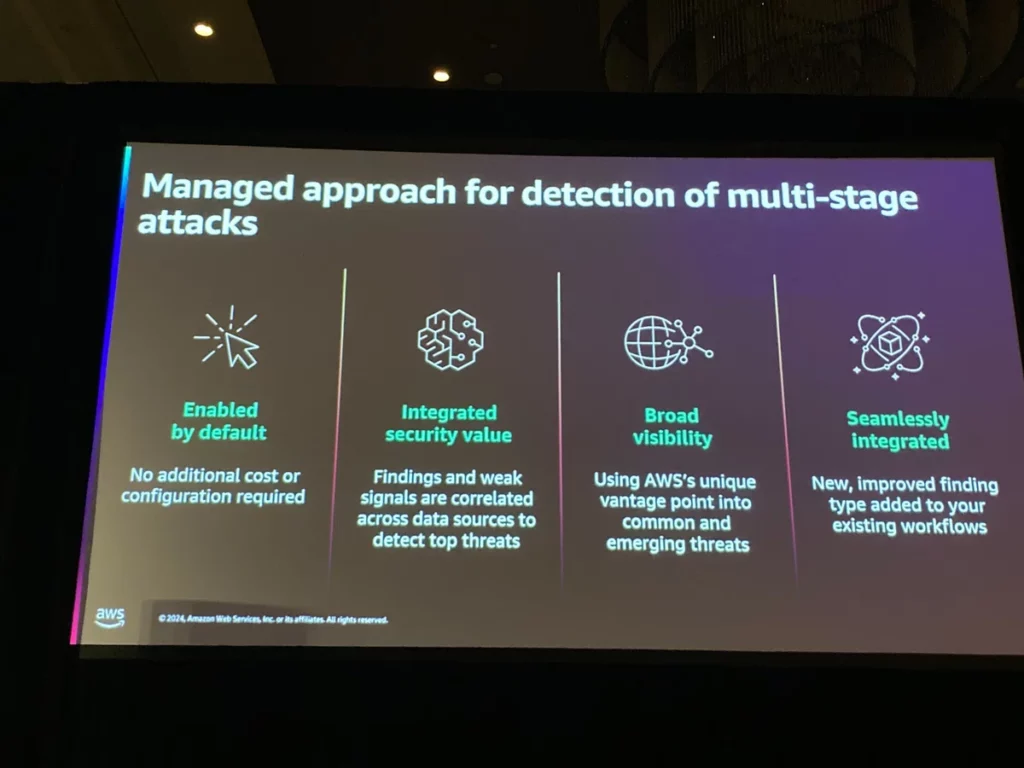
検出可能な攻撃シーケンスとして以下3つが列挙されていました。
- 認証情報の侵害に関連する攻撃シーケンス
- データ侵害に関連する攻撃シーケンス
- EC2インスタンスのランタイムモニタリングを使用した攻撃検出
(近日公開)

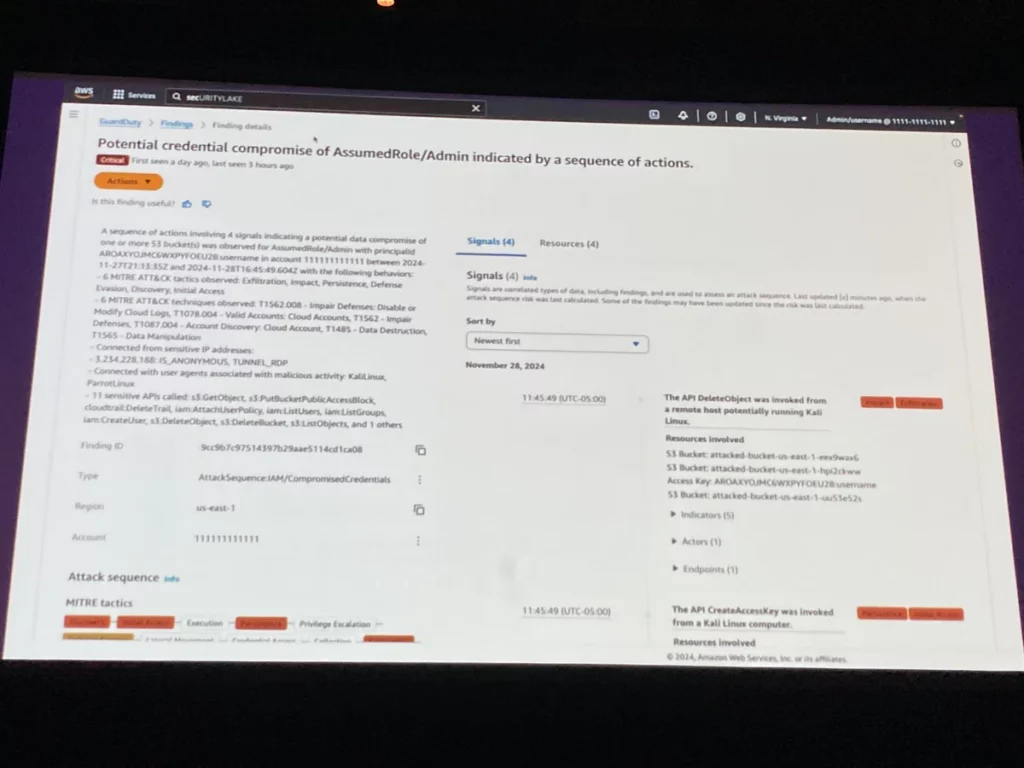
GuardDutyのマネジメントコンソールで攻撃シーケンスの個々のアクティビティのタイムライン、関連リソース、指標が一覧表示されます。
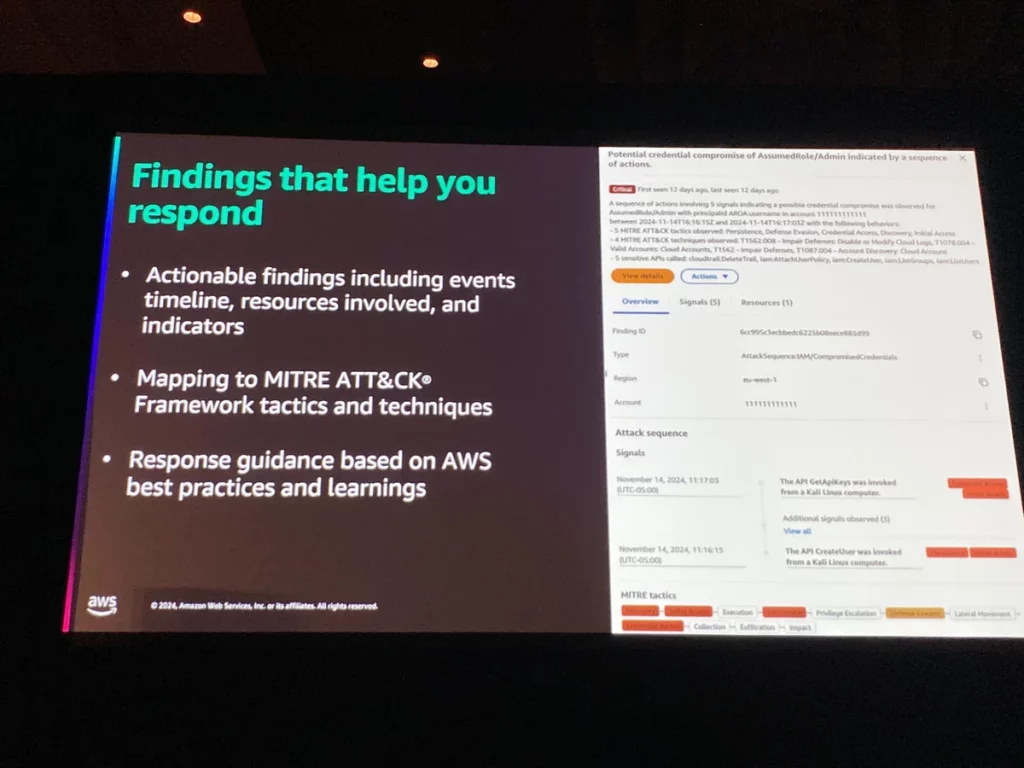
またMITRE ATT&CKフレームワークとマッピングしてくれるので、いま現在どの種類の脅威が発生しているか、次に何のアクションを実行すべきかを素早く判断できそうです。
セッション後半ではシニアプリンシパルサイエンティストの方から、本機能の脅威検知に用いられている仕組みについて説明がありました。
詳しいことは把握できなかったのですが、機械学習と表現学習を活用して異常を検知しているとのこと(新規アクティビティであっても同様のAPIコールパターンや同じリージョンからのアクセスは必ずしも脅威とは判断しない等)。
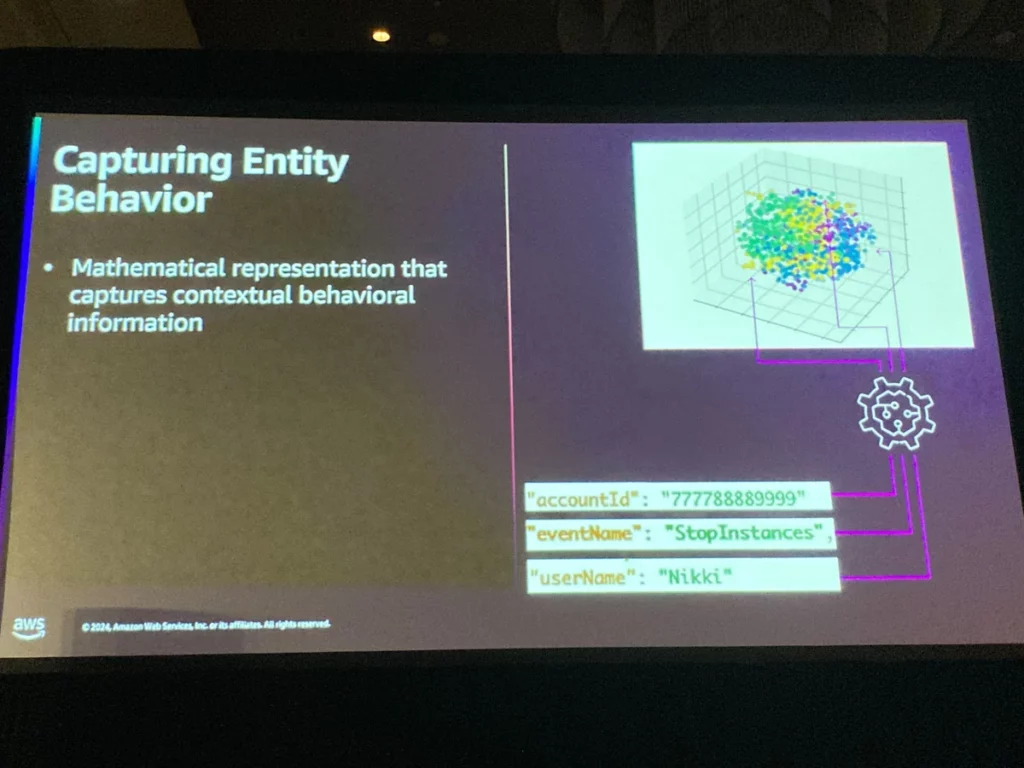
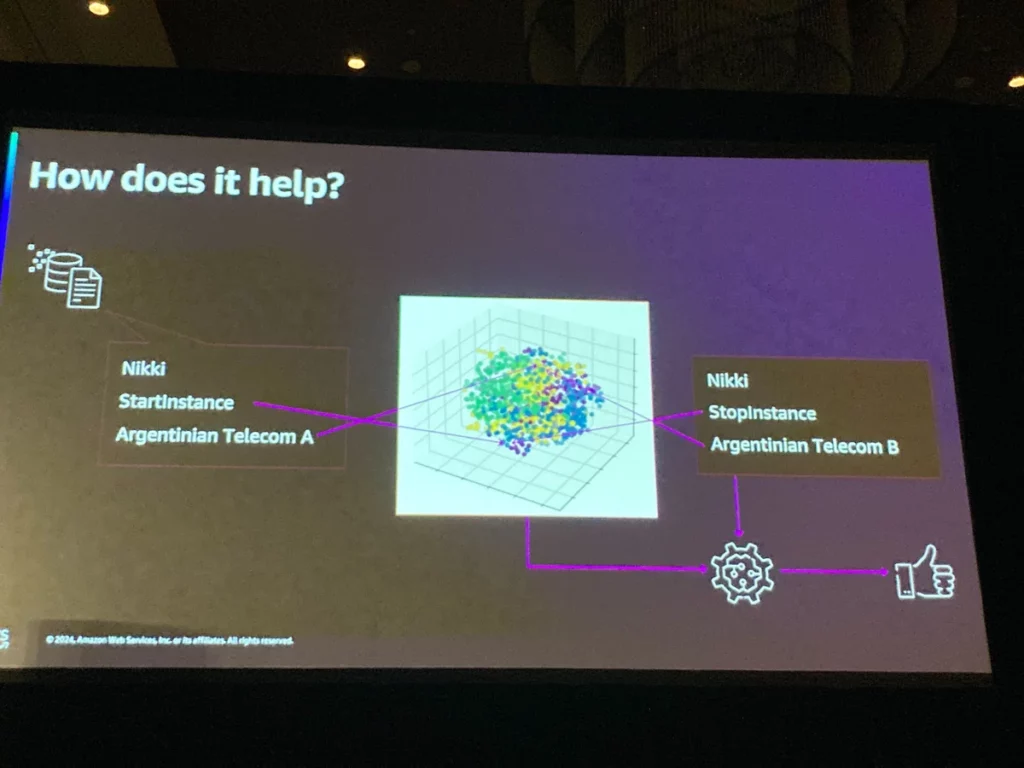
さらにセキュリティ専門家の判断プロセスをマーカーと呼ばれる関数として実装。抽出されたセキュリティシグナルをマーカーで評価、ランキングをスコアリングして重要度を判断しているとのこと。
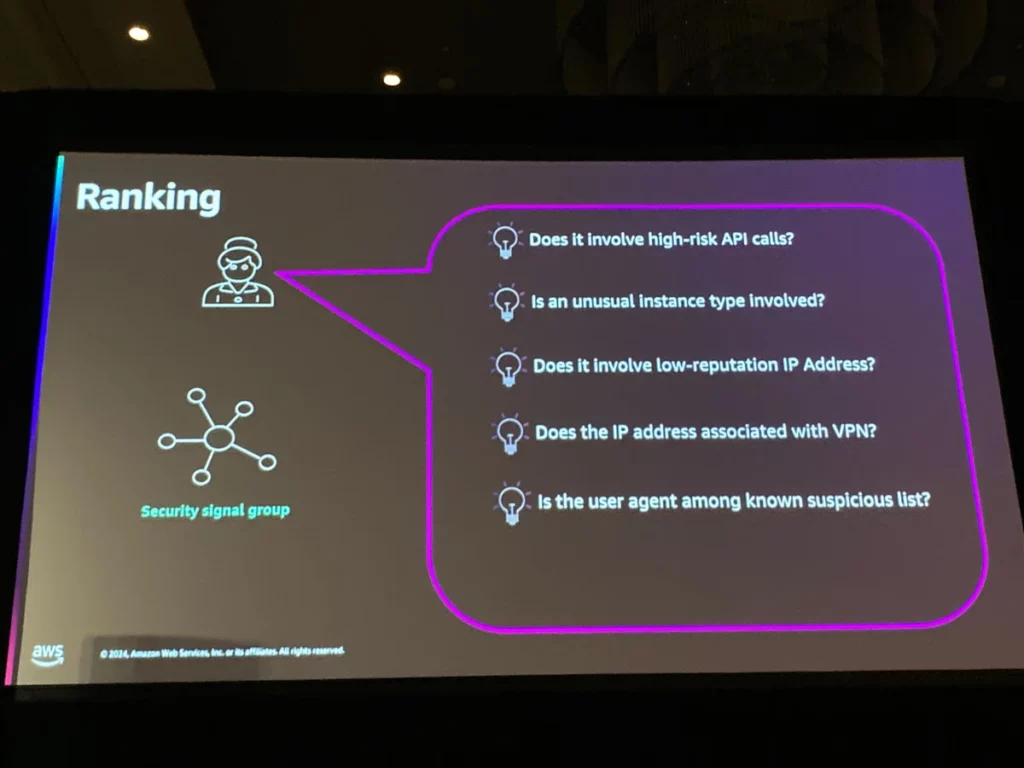
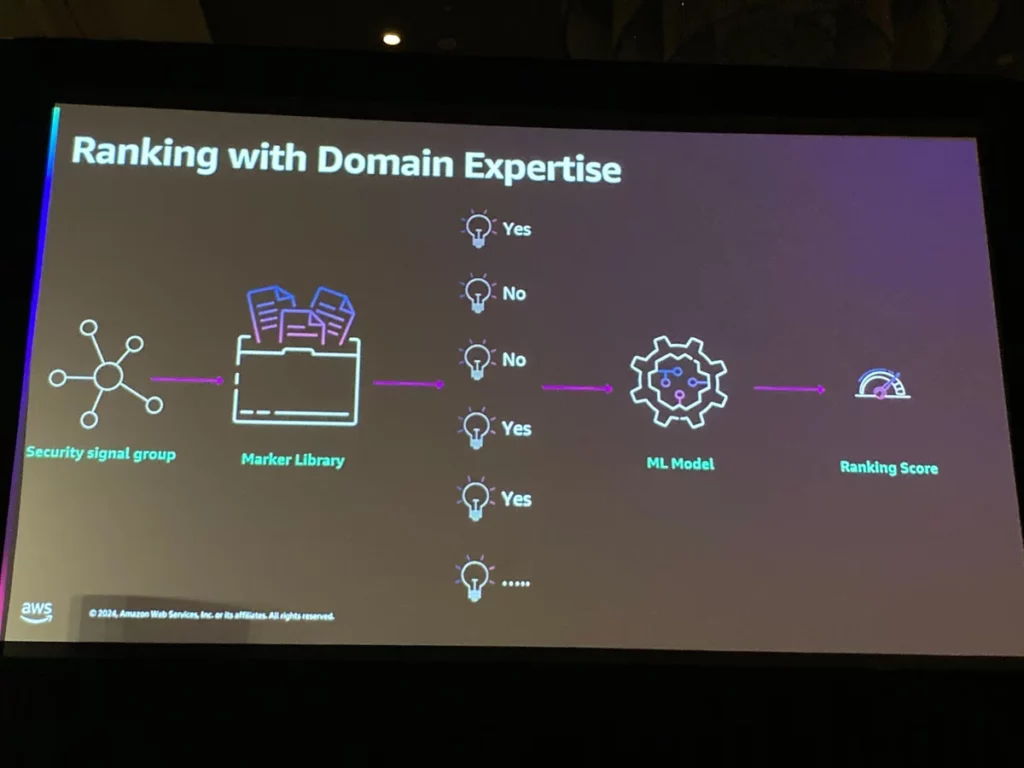
所感
昨今急増しているサイバー攻撃を未然に防ぐために不審なアクティビティの早期検知は必要不可欠です。
GuardDutyの本アップデートは、運用しているシステムで発生した脅威状況が把握しやすくなるのはもちろんのこと、従来セキュリティチームが行っていた煩雑な一次分析の負荷を軽減して最も優先度の高い脅威に取り組めるようになるので、より効率的に対応がとれるようになります。
本機能はデフォルト有効で追加費用もかかりませんので、すでにGuardDutyを利用している企業にとって非常に嬉しいアップデートですね!
まだGuardDutyを利用していない企業はこれを機会に検討してみる価値はあると思います。
関連ページ
AWS・Azure・GoogleCloudの
セキュリティは





